Click the Exhibit button.
-- Exhibit
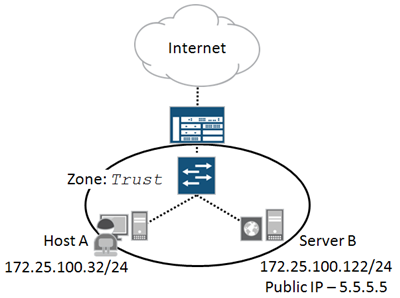
-- Exhibit --
Referring to the topology shown in the exhibit, which two configuration tasks will allow Host
A to telnet to the public IP address associated with Server B? (Choose two.)
- A. Configure transparent mode to bypass the NAT processing of Server B's public IP address.
- B. Configure a stateless filter redirecting local traffic destined to Server B's public IP address.
- C. Configure a destination NAT rule that matches local traffic destined to Server B's public IP address.
- D. Configure a source NAT rule that matches local traffic destined to Server B's public IP address.
Answer : C,D
Explanation:
In this scenario we have a host be accessible on the Internet by one address, but have it be translated to another address when it initiates connections out to the Internet.So we need to combine Source and destination NAT.
Reference:
http://chimera.labs.oreilly.com/books/1234000001633/ch09.html#destination_nat
Your SRX device is performing NAT to provide an internal resource with a public address.
Your DNS server is on the same network segment as the server. You want your internal hosts to be able to reach the internal resource using the DNS name of the resource.
How do you accomplish this goal?
- A. Implement proxy ARP.
- B. Implement NAT-Traversal.
- C. Implement NAT hairpinning.
- D. Implement persistent NAT.
Answer : A
Explanation:
Reference : http://www.juniper.net/techpubs/software/junos-security/junos- security96/junos-security-swconfig-security/prxy-arp-nat_srx.html
Which action will allow an administrator to connect in band to an SRX Series device in transparent mode over SSH?
- A. Use a VLAN interface.
- B. Use the loopback interface.
- C. Use a logical interface.
- D. Use an irb interface.
Answer : D
You want to create a custom IDP signature for a new HTTP attack on your SRX device.
You have the exact string that identifies the attack. Which two additional elements do you need to define your custom signature? (Choose two.)
- A. service context
- B. protocol number
- C. direction
- D. source IP address of the attacker
Answer : A,C
Reference: http://rtoodtoo.net/2011/09/22/how-to-write-srx-idp-custom-attacksignature/
Click the Exhibit button.
-- Exhibit
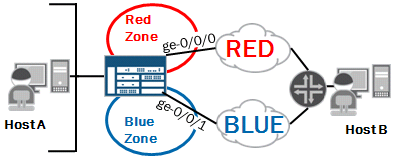
-- Exhibit --
TCP traffic sourced from Host A destined for Host B is being redirected using filter-based forwarding to use the Red network. However, return traffic from Host B destined for Host A is using the Blue network and getting dropped by the SRX device.
Which action will resolve the issue?
- A. Enable asyncronous-routing under the Blue zone.
- B. Configure ge-0/0/1 to belong to the Red zone.
- C. Disable RPF checking.
- D. Disable TCP sequence checking.
Answer : B
Reference: https://kb.juniper.net/InfoCenter/index?page=content&id=KB21046

